Cyber Jawara High School 2024 Final
Cyber Jawara is a national CTF held by CSIRT.id and Indonesia Network Security Association. It’s quite a well-known competition, as it has ran for more than a decade now, and there’s a competition division for high school students!
All solve is by me :p
We were so close to getting to top 3, but…
Well, maybe next time,
though genggx. managed to upsolve a pwn chall minutes after it ends ;;
Also, this might be the first write-up only available on my blog!! (i.e. no gdocs ver.)
You can get the challenges files on my CTF repo!
Anyway, happy reading!! :DD
REVERSE ENGINEERING
[140] Camel White [12 Solves]
Summary
OCaml fibonacci optimization!
Solution
We’re only given one file, main.ml:
|
|
So, let $f_{n}$ be the $(n + 4)^{th}$ fibonacci number.
This means, $f_{2}$ is $5$,
because the fibonacci sequence starts with $0, 1, 1, 2, 3, 5$,
and the sixth one is $5$!!
A bit weird, but that’s just how it’s here.
What it does is simply print the hexadecimal value for each $n$ defined as data there,
and encapsulate them with CJ{}, the flag format.
Now, why don’t we just run it?
Because this is unoptimized!
It’ll take a really long time for the program to calculate the fibonacci numbers.
The solution here is to simply optimize the fibonacci function, f:
|
|
Yup!! That’s all it takes.
I had to download ocaml to run this,
but other than that, just run the optimized code!!
Flag: CJ{401709b206b04f4c2ecdb29ab0c75b437d2a04e5fe72d81a0fdc45bca02e710d983c}
Rating: [4/10]
I tried making the solver in python,
but because it has no limit on the size of integer,
the resulting flag is wayy wayy longerr,
so it’s wrong!
I don’t understand the syntax,
but as always,
the Transformer NN is there to help :>
[500] 🩸 Gudang Garam 🩸 [1 Solve]
Summary
aarch64 asm to C, as always, then rev it, EZZ…
Solution
So, the given asm file is quite big,
|
|
2175 lines 💀💀
Most of it are just data though.
Doing this manually would be tiring, isn’t it?
Just give an ’expert system’ the main and check function!
Gemini turned it to C:
|
|
You can clearly see main just checks for input length,
then passing the first argument argv[1] to check.
Our input is using program argument,
as in ./garam CJ{flek}.
It has to be 44 (0x2c) chars.
Also, that’s quite a low level definition of check.
It checks input length again (useless),
then iterate 44 times to calculate $\Sigma_{0}^{43} f_{i} \times X_{i}$,
but it’s unclear how it access X.
If you notice something on Gemini’s output,
it multiplies index local_8 (outer loop) with 0xB0 (176).
Since the size of each element is 4 bytes (see asm code),
then $\frac{176}{4} = 44$.
Ahh!!
So, X is an 2D array of $44 \times 44$ size!
Let’s see what the other say about this.
Claude give us this for check:
|
|
It successfully identifies X as a 2D array.
Immediately, I realize what Y actually for here.
I can express it like:
$$\left( Y_{i} = \Sigma_{j = 0}^{43} f_{j} \times X_{j,i} \right) \forall i \in \{0,1,…,43\}$$
I know you get what that means ;)
Like, do I need to explain it?
The code should be enough.
Now, just turn the asm X to a 2D python array,
and also Y,
then with known values CJ{},
we use Z3 to solve it!
It’s simple really, here’s the solver:
|
|
Flag: CJ{3928ee5e0db2daa3eb87c6bee7c14e20d5f7d906}
Rating: [6/10]
I’m writing this write-up on the train lol. It’s 22:42 right now. Gotta sleep :p
Misc
[410] Baby Pyjail [4 Solves]
Summary
A standard no builtins pyjail, without length limit.
Solution
So, we’re given these files: Dockerfile, which contains instructions for building an Docker image;
docker-compose.yml, which ‘define and share multi-container applications’;
‘flag.txt’, our read target, locally contains REDACTED; and
jail.py, the Python code for the jail itself.
Let’s see the docker files first!
|
|
This setup the docker image.
You can see at line 10, it rename the file with a random md5sum.
So, this means that we need to at least ls the file system to know the actual name in the remote instance.
|
|
So, I guess we’re privileged, hehe. You can’t delete the flag file though, since it was set to read-only for all users (including root).
Aight, now how about the jail itself?
|
|
Really short, it just sets __builtins__ to None,
effectively deleting it.
built-in functions like open or import is gone.
But, we can recover builtins,
as object types still exists,
like (), a tuple,
or ‘""’, a str.
I debug this locally by building the docker,
and modifying jail.py to print the result of the payload,
either exception or ran.
I also add i to the e globals argument,
so I can call it to see what an expression returns.
You can see these with the commented codes above.
I started with getting the object class,
|
|
Got it!
Now, we’re using object introspection.
This can be done by calling __subclasses__()
to list all loaded classes in memory.
We’re looking for os, subprocess, or open.
|
|
Whww, that’s a really long one :v
There’s none of the classes specified earlier,
but there’s _io and _frozen_importlib.
I first tried _io and its modules,
but none seems to work,
and that also the flag name is unknown.
So I went with _frozen_importlib instead,
and Arcanum said these functions are interesting:
_frozen_importlib.BuiltinImporter_frozen_importlib.FrozenImporter_frozen_importlib_external.FileLoader_frozen_importlib_external.FileFinder
If I tried FrozenImporter,
it doesn’t seems to have any useful modules…
|
|
What works was BuiltinImporter,
which has the sys module!! :o
|
|
There’s even builtins there!!
But here,
I just use posix that allow me to execute shell commands
with its system method.
|
|
That’s the local flag :>
Now, just do it on the remote instance!
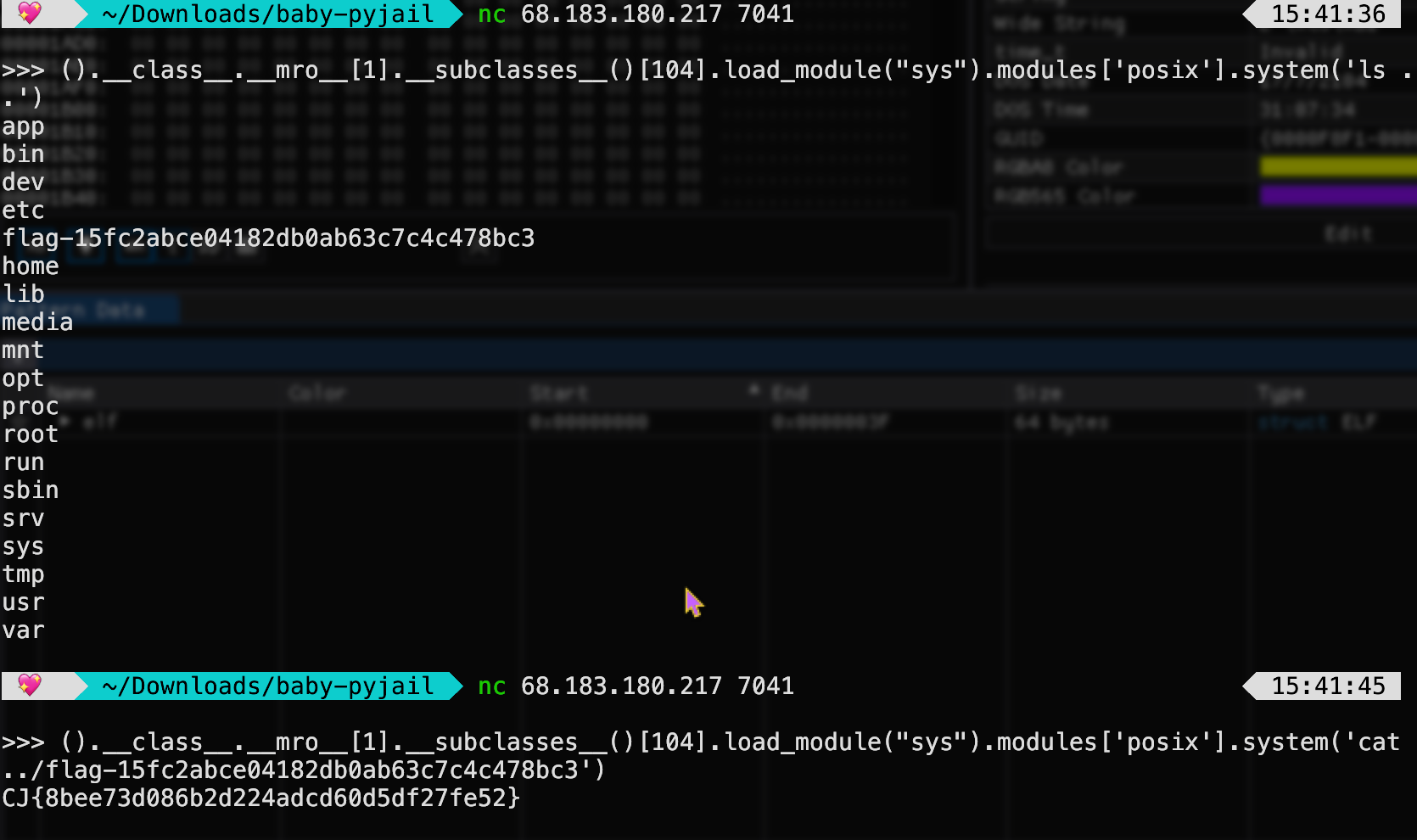
Flag: CJ{8bee73d086b2d224adcd60d5df27fe52}
Rating: [8/10]
Pyjail is kinda fun ngl, I might make it my second cat., dawg :p
Forensics
[500] ⌛️ C2 ⌛️ [0 Solve]
Summary
Upsolved! Given a .pcap, we extract a C2 backdoor binary, and with incoming openssl AES-128 ECB encrypted commands, get the flag as one of the decrypted command.
Solution
WIP
By the way, one guy just solve the chall with one command 🥶🥶
|
|
What a lad.
I gotta learn openssl for real duhh.
Flag: CJ{8c05db2894cde846f4967bfa0274ad177d6e9f95b26d442c7046f8e7ea5c929f}
Rating: [6/10]